
If you consider yourself a geek, or aspire to the honor of geekhood, here’s an essential checklist of must-have geek skills.
The term ‘geek’, once used to label a circus freak, has morphed in meaning over the years. What was once an unusual profession transferred into a word indicating social awkwardness. As time has gone on, the word has yet again morphed to indicate a new type of individual: someone who is obsessive over one (or more) particular subjects, whether it be science, photography, electronics, computers, media, or any other field. A geek is one who isn’t satisfied knowing only the surface facts, but instead has a visceral desire to learn everything possible about a particular subject.
A techie geek is usually one who knows a little about everything, and is thus the person family and friends turn to whenever they have a question. If you’re that type of person and are looking for a few extra skills to pick up, or if you’re a newbie aiming to get a handhold on the honor that is geekhood, read on to find out what skills you need to know.
1. The Meaning of Technical Acronyms
- USB – Universal Serial Bus
- GPU – Graphics Processing Unit
- CPU – Central Processing Unit
- SATA – Serial ATA
- HTML – Hyper-text Markup Language
- HTTP – Hypertext Transfer Protocol
- FTP – File Transfer Protocol
- P2P – Peer-to-peer sharing (See http://en.wikipedia.org/wiki/P2P)
2. How to Reset RAM
If you rolled your eyes here, that is a good thing. If not, you have many things to learn, young padawan. It’s amazing how few people know how to do this. If you’re unsure, hit up the link below to find out how:
http://www.ehow.com/how_4473936_reset-ram-computer.html
This tip is only really good for older machines running 9x based OS’s. However if you are running Windows Vista this can have a problem with RAM so here is how to create a desktop shortcut to free up RAM.
1. Right-click on your desktop and select New > Shortcut.
2. Copy/paste the following into the box: %windir%\system32\rundll32.exe advapi32.dll,ProcessIdleTasks
3. Click Next, name it ‘Clear Memory’, and click Finish.Give it asuitable icon so it looks nice.
3. Identify Keyloggers
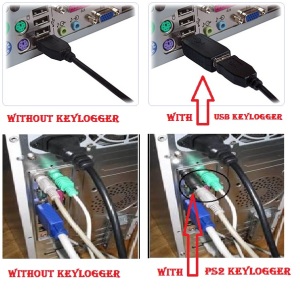 Internet cafes are the most likely place you’ll find them, followed by library, perhaps, and maybe even you own house if you’ve some unscrupulous friends/family. Identity theft groups warn about keyloggers and advocate checking out the keyboard yourself before continuing. Can you identify a keylogger, however, if one is plugged into the back of the system?
Internet cafes are the most likely place you’ll find them, followed by library, perhaps, and maybe even you own house if you’ve some unscrupulous friends/family. Identity theft groups warn about keyloggers and advocate checking out the keyboard yourself before continuing. Can you identify a keylogger, however, if one is plugged into the back of the system?
Here’s what one looks like:
Hit up this link for excellent info on keyloggers on public computers and how to protect yourself:
, http://www.ghacks.net/2007/06/28/how-to-defeat-most-keyloggers-on-public-computers/
4. Surf the Web Anonymously
We won’t make any assumptions about why you may need this particular skill, but the fact remains that every geek should know how to traverse the Internet with the highest amount of security possible.
Aside from the safest method–which is using a connection that is not yours–you will need the ultimate in proxies…Tor. Tor is an onion-routing system which makes it ‘impossible’ for someone to find out who you actually are.
5. Bypass a Computer Password on All Major Operating Systems
Obviously you shouldn’t use this to gain unlawful access to a computer. If you’re a geek, however, you’ll eventually end up in a situation where someone forgets their password, you acquire a machine with an operating system you cannot access, or similar situation.
See this tutorial for info on how to bypass the password on the three major operating systems: Windows, Mac, and Linux.
http://www.joetech.com/2009/01/29/how-to-crack-the-account-password-on-any-operating-system/
6. Find a Users IP Address on AIM
Knowing someones IP address is actually pretty useless in this case, but most people don’t realize that. If someone is harassing you via AIM and you can’t get them to stop, discovering their IP and sending it to them–with a nicely worded threat of law enforcement involvement should they not stop–is likely enough to send them scamping away with tail between legs.
http://www.elitehackers.info/forums/archive/index.php/t-2827.html
7. Hide a File Behind a JPEG
So you need a nice spot to hide your blackmail personal files. You could, of course, bury them deeply within a series of random, useless folders, but there’s always the chance of them being discovered. A password protected RAR is the best choice, but it’s a bit obvious despite the most boring title you could give it.
A sneaky person would hide the important file behind a completely random and boring family reunion photo, where no person in their right mind would shift through.
http://www.online-tech-tips.com/computer-tips/hide-file-in-picture/
8. Crack a Wifi Password
This is one of those things you don’t need to do (hopefully), but that you still need to know just for the sake of knowledge. A strong WPA password is very secure, but most people don’t want to bother learning a convoluted series of letters, numbers, and symbols, instead opting for random everyday words.
A good overall tutorial on wifi and cracking can be found here: Cracking_WEP_and_WPA_Wireless_Networks
9. Monitor Network Traffic
The Internet is a vast place with a bit of everything. Whether you’re curious about what your roommate is downloading, your kid is getting into, or any leeches living around you who’ve unscrupulously breached your wifi, knowing how to analyze network traffic is an invaluable skill.
Here is a list of dozens of network analyzers, as well as some general info to get you started: http://www.slac.stanford.edu/xorg/nmtf/nmtf-tools.html
10. Recover Master Boot Record
A virus or other problem can lead to an MBR error, which will make it impossible to access install. Many users would simply become frustrated and reinstall, but not you! Every geek should know how to recover the master book record.
Here is an excellent guide to get started: http://www.ntfs.com/mbr-damaged.htm
11. Retrieve Data off Hard Drive
There will come some point in your life when a hard drive craps out sans warning. It could be due to a number of reasons–physical damage, file corruption, etc. There are computer service centers that would be happy to extract the data for a (hefty) fee; a true geek would be the one working at center, not taking his or her drive there.
To find out how to retrieve data off a damaged hard drive, read here: http://www.ehow.com/list_7225818_5-off-crashed-hard-drive.html
12. Load Rockbox onto an MP3 Player
The firmware that comes on your average mp3 player is intended for those who are scared of advanced features; often, the only audio settings available are a few prearranged EQs. If you’re an audiophile–or simply frustrated with the lack of control over your music settings–Rockbox is the firmware for you. Open source and free, it can be installed on several different types of players and enables full control over what you listen to.
13. Unbrick a Smartphone
No geek can resist the allure of flashing the newest beta firmware onto their shiny smartphone. The byproduct of that is sometimes a bricked phone, which would leave many sobbing into their pillow at night. To avoid rendering your $400 gadget into a door stopper, learn the fine art of unbricking and then flash away.
As the method used to fix a phone will vary, this is the best place to start looking for answers: http://www.howardforums.com/
14. Replace a Laptop Keyboard
Keyboards get gummy after awhile. If you use yours a lot (aka: all day), then you probably eat over it at some point. Crumbs get into the keys and things are sticking, and before you know it, you need a new keyboard.
http://www.refurbished-laptop-guide.com/how-to-remove-a-laptop-keyboard.html
15. Rip Streaming Videos
Streaming videos are officially in vogue. We’re not going to make any assumptions about what type of videos you are streaming and may want to keep, but no matter what it is, any geek could rip them while sipping a Red Bull and watching the latest episode of BSG.
Here’s a hint to get you started: http://applian.com/download-videos
or try this one http://www.downloadyoutubevideos.com
16. Strip Windows DRM
DRM is incredibly annoying. With many online stores now offering DRM-free mp3 audio files, it would seem it’s not as big of an issue as it used to be. That is not not the case, however, with all videos bearing a DRM as well as music of a higher-quality than MP3.
Stripping Windows DRM is not legal. If you’re a geek, your probably don’t care: http://undrm.info/remove-DRM-protection/FairUse4WM-freeware-DRM-removal-Windows-software-Strip-copy-protection-from-WMV-ASF-WMA-Windows-Media-Player.htm
17. Homebrew Hack Game Systems
Gaming consoles are notorious for having features you can’t use simply because the manufacturer decided to lock them down. As a geek, you can’t just be satisfied with the features they decided to give you. No, you have to crack that case open and take a peek inside. Every geek should know how to homebrew hack their system and unlock it’s full potential.
18. Find a Website IP Address Without Web/Command Prompt Access
Some school admins think they’re being sneaky when they lock down the command prompt and block all major IP search websites and block all the websites you actually want to visit. Of course, that is child’s play for any geek.
First, to get a new command prompt, open Notepad and type: command.com. Then, save as “cmd.bat”. You now have a command prompt.
Now, open the command prompt and type “ping http://www.website.com/” to find the IP address of that website.
Enter the website into the browser and you will officially have impressed all your friends.
19. Bypass School or Work Website Blocks
What is a horrific situation for an average computer user is a simple irritation for an everyday geek. To bypass a website block/filter, simply enter that websites IP address in instead of the actual site address.
20. Screw with Wifi Leeches
Nobody likes a wifi leech. At best, they’re simply using up your valuable bandwidth. At the worst–and far more likely, they’re stealing your identity and watching your activities. After watching your network and identifying the leech, use this trick to flip their browser upside down and let them know you don’t appreciate the intrusion.
http://tech.nocr.at/hacking-security/baffle-wifi-leeches-with-an-upside-down-ternet-2/
21. Hexadecimal and Binary Number Systems
Everyone knows the normal, everyday digit system used. It takes a special–possibly psychotic person–to also know hexadecimal and binary number systems.
Here is an excellent interactive tutorial on learning the two systems: http://www.wisc-online.com/objects/index_tj.asp?objID=DIG1102
22. How to Hot Wire a Car
If your family always turns to you any time their computer hiccups, their DVD player needs fixed, or their home security system doesn’t activate, it’s only a matter of time before someone asks you how to hot wire a car. Wouldn’t it be great to be able to answer them?
To learn this unique skill, read here: http://howto.wired.com/wiki/Hot_Wire_Your_Car
23. Increase Wifi Range
With so many small portable gadgets gaining more and more sophisticated web browsers, in addition to gaming systems like the PSP and DS, getting the most use out of your wifi is practically a geek necessity.
Here is a good guide on extending your wifi’s range: http://www.mavromatic.com/archives/000451
24. Carrying a Computer Cleaning Arsenal on Your USB Drive
A good geek prepares for their friends stupidity. No matter how many times you tell them to stop downloading porn, they keep doing it until their machine is so infected it can’t drag itself into a grave. An arsenal of portable malware cleaners, a portable task manager, anti-virus, etc, will make those impromptu purging sessions all the easier.
25. Running an Operating System from a USB Thumb Drive
Most people don’t even understand what the magical operating system is. As a geek, you should transcend that basic knowledge and have a small operating system on your thumb drive handy for those times you need computer access but don’t know the password to a nearby computer.
26. Understand What “There’s no Place Like 127.0.0.1” Means
A lot of geeks wear this shirt as a short hand code for their computer finesse–or maybe just to screw with other people who stare but cannot figure out what it means. No matter the reason, if you’d like an answer, check out the link below.
http://www.tech-faq.com/127.0.0.1.shtml
27. Read 1337 At Normal Speed
Sure, everyone knows about it and it’s no longer cool, but if you’re going to proclaim yourself as a geek, you should be able to read it full speed. Who wants to choke in front of the wannabe that learned to read it full speed and flaunts it in your face?
http://www.wikihow.com/Read-and-Write-in-1337
28. At Least One Fictional Language
And not only should you know a fictional language, but you should use it to say something about yourself. Do you choose Klingon or Quenya?
Here’s a list of constructed languages: http://en.wikipedia.org/wiki/List_of_constructed_languages
29. How to Survive in a Linux Argument
Linux is gaining an all around higher standing in the geeksphere, and it’s bound to enter a conversation at some point (which will invariably end up turning into an argument). If you want to keep up, you’ll need to understand the basic points of Linux, as well as the general info of all basic things.
Here’s a good place to read and gain a foothold: http://www.linux.com/articles/feature/
30. Identify Major Constellations
For those times you venture from the air-conditioned, computer filled basement of your parents house (or something like that), look up at the stars and have yourself a Galileo moment. The stars may just be dots to many people, but with the handy website below, you’ll be stopping man-belts and lions in no time.
http://www.sky-watch.com/astronomy-guide/major-constellations.html
31. Use a Camera in Manual Mode
Sure, you could just use auto mode like everyone else too afraid to learn what some letters and numbers mean, but then you wouldn’t be much of a geek, would you? The oft-ignored dial on a camera is the key that unleashes the best quality photos possible, and every geek should be a whiz at using one.
http://digital-photography-school.com/digital-camera-modes
32. Who Mulder and Scully Are
It seems that in the plethora of geek websites, there always appears a joke about Mulder and Scully, the two main characters from the X-Files. If you don’t know who they are, you’ll be left in the dark, alone, contemplating what exactly it was you were doing in the 90’s that you wouldn’t understand the joke.
http://en.wikipedia.org/wiki/Mulder_and_Scully_(song)
33. Javascript
HTML is running the world (not really). Everyone knows some HTML and it makes them feel empowered. As a geek, you want to transcend that basic knowledge others share and know a little more. JavaScript is the answer–it is easy to learn if you’re not actually interested in web programming, but simply curious, and it looks scary to anyone who doesn’t know it.
http://www.yourhtmlsource.com/javascript/basicjavascript.html
34. How to Unlock an iPhone
Sure, most geeks wouldn’t be caught dead with an iPhone, but what about your friends? You’re the smart techie, they’ll expect your to know how to unlock it.
http://www.pcworld.com/article/137223/how_to_unlock_an_iphone.html
35. How to Install Mac OS X on a PC
Just because you don’t want Mac on your PC doesn’t mean you shouldn’t know how to do it. Knowledge is power, right? Go ahead, use this to stump your friends and family.
http://dailyapps.net/2007/10/hack-attack-install-leopard-on-your-pc-in-3-easy-steps/
36. Build a PC
If you purchase a ready-made PC, you can be sure of one thing–you’re paying more than you should. Assembling your own PC isn’t too hard, and is the first thing you should be aiming to accomplish as a geek.
Here is a massive article on assembling your own PC: http://www.pcmech.com/byopc/
37. Tethering a Smartphone
Nothing like a little wifi on the move, eh? Tethering a smartphone means using the Internet on your laptop/netbook via your cell phone. Of course, the method to do this depends on your phone, but here’s an article to get your started:
http://www.tech-recipes.com/rx/2276/smartphones_bb_treo_tether_modem_usa_carriers/
38. Wiring a Home Theater System
Home theater systems used to consist of a TV and a chair. Gone are those days of simplicity, however, and setting up a modern system can be pure mind-boggling horror. Where does the modulator go, why does the DVD player have no video and the cable box no sound?
Here’s a tutorial, including excellent diagrams, to show you how: http://www.prillaman.net/ht_info_8-wiring.html
39. Replacing a Laptop LCD
Laptop LCDs are vulnerable to many different mishaps: accidental pressure spots, shadows, airsoft pellets…. No matter, there will come a point when you need to swap your LCD for a new one. Now, as a geek, you probably don’t have an extended warranty. If that’s the case, here are some excellent pages and pictures on replacing the display:
http://www.fonerbooks.com/laptop_4.htm
40. Make a Laptop Cooling Pad
Can you believe these cost $50?! A geek will need one, because data crunching/DVD ripping/videos playing/rendering at the same times tends to cause excess heat. Instead of shelling out your hard earned dollars, make your own like so: http://www.instructables.com/id/Lazy-mans-laptop-cooler/
41. Unleash a Laser Pointer’s full potential
A normal person uses a laser pointer to drive their dog crazy. A geek uses it to melt butter for their grilled cheese sandwich. To unless a laser pointer’s full strength, crack open the case, fry the resistor with a hot soldering iron, then snap it back together and keep it away from flesh/eyes/airplanes. The pointer will burn out after a few hours, but what a fun few hours they will be.
Note: this is dangerous. Don’t do anything stupid.
42. Keyboard Shortcuts
This will depend on your operating system and the apps you use, so there’s no tutorial available. However, that is irrelevant–you’re a geek, you can find them yourself. Shortcuts are the difference between a slow computer user and a geek. The geek will always will out in a speed contest, because they do practically everything from their keyboard.
43. Soldering Glasses Together
Nerds use tape on broken glasses; geeks use solder. ‘Nuff said.
44. How to Execute a Shell Script
If you’re a true geek, you’ll need to do this at some point. Below are instructions on how to do so. Remember: always be cautious when running a script, you don’t want your computer to turn into a door stop, now do ya?
http://www.mcsr.olemiss.edu/unixhelp/scrpt/scrpt1.2.html
45. How to Hack a Pop Machine
Okay, so stealing isn’t cool. Still, hacking is simply a misunderstood art, right? So hacking a pop machine isn’t really stealing, because it’s not about the pop, it about the pleasure of getting your way. Or something like that. (Newsflash, it is illegal, don’t do it.) If you want to try your fingers at getting a free Coke, check out this link:
http://skattertech.com/soda-machine-hack/
46. Turn a Laptop into a Digital Picture Frame
So you want to show off pictures of your dog and that girl you once met, but you want to do it in an uber geeky way. Any schmuck can go to Walmart and buy a digital picture frame for a grossly inflated price. But you…oh, you’re too smart for that. No, instead you’ll find an old laptop on eBay for $5 and turn it into a true work of art.
http://repair4laptop.org/notebook_picture_frame.html
47. How to Mod a Flash Drive Case
All the geeks are doing it…. Whatever. The case your flash drive came in is probably weak and most certainly plain. Why not jazz it up with your own unique style?
Here’s one such case mod, and dozens of related projects: http://www.instructables.com/id/Metal-USB—Flash-drive-case-mod/
48. Do Cool Things to Altoids Tins
People are obsessed with these things. Altoids tins are durable, small, and just begging to be filled with LEDs, mp3 players, audio amps, and maybe some snuff. A good geek will find millions of uses for these little metal wonders. If you need a mental boost, however, here’s some interesting links:
http://www.squidoo.com/altoids-tins
49. Convert Cassette Tapes to Digital Audio Files
If your geekhood started in the 90’s, then you probably have a least a few (dozen) cassette tapes still sitting around. Why not breathe digital life into them before they fall ill to mortal fate?
http://lifehacker.com/software/mp3/alpha-geek-how-to-digitize-cassette-tapes-222394.php
50. Lock Your Computer with a USB Drive
You don’t want anyone getting into your files while you’re gone. A normal password would be enough to keep most people out, but what if you got super-secret X files on your computer? You can lock your machine down with a USB drive via these instructions:
http://lionjkt.wordpress.com/2008/12/31/how-to-lock-your-computer-with-usb-drive/
51. Run Your Own Ethernet Line
Wifi has taken the place of a wired connection in many homes, and with good reasons–you can go anywhere, no cables necessary. What about those…sensitive…activities that you’d rather the neighborhood script kiddie didn’t see on your wifi? An Ethernet cable is your solution.
To wire your own Ethernet, hit up this link: http://www.ertyu.org/steven_nikkel/ethernetcables.html
52. Set Up a Streaming Media Server
With digital files becoming the ultimate medium, many people have hundreds of gigabytes worth of music, videos, and pictures. You could keep them on a portable hard drive, but then you’re have to take it everywhere, and only one person could use it at a time. The solution is a streaming media server, something no geek can live without.
http://www.n00tz.net/2008/07/vlc-media-server-ubuntu-hardy/
53. Setting up a VPN
If you’re like most geeks, you can’t live without your computers. They store your life in some poetic fashion, holding files you feel a personal connection with…. Anyway, if you are at work and suddenly realize you left an important picture at home (or you need blackmail material pronto), having a VPN ready to go will save you big time.
http://www.computernetworkinghelp.com/content/view/41/1/
54. Turn Webcams into Security Cameras
Is someone stealing your Netflix DVDs? Do you suspect it is a fat hairy man in his boxers taking them each morning? If so, you can get your proof using a couple webcams and a bit of software.
55. Control Your House Lights with a Computer
Controlling the lights in your house via computer is a great way to freak out the neighborhood kids ding-dong-ditching (assuming you wire up a Halloween scream motion sensor, also). If you reasons are less nefarious, you simply use it to turn on and off lights without having to life ye butt from thy seat, which is a good reason in itself.
http://www.instructables.com/id/Control-lights-in-your-house-with-your-computer/
56. Play Retro Games without Retro Consoles
This applies to the geeks who enjoy gaming. Setting up an emulation PC on your TV is a great way to relive those games of old.
57. Put LEDs Inside a Lightbulb
The days of hot incandescent and mercury-laden fluorescent are gone, and in are the days of long lasting, low heat, low consumption LEDs. As any good geek, you want to be able to say “I was doing X long before it became mainstream.” Here’s your chance–the following link will show you how to put an LED inside a lightbulb, something sure to stump your friends the same way Grandpa’s ship-in-a-wine-bottle used to stump you.
http://blog.makezine.com/archive/2006/06/make_a_led_bulb.html
58. Create Music with Keyboard
How awesome is KeyBored? This little app gives all of your QWERTY keys a piano note. When you type, it sounds like an infant monkey punching a keyboard. If you’ve got some musical chops, it won’t take you long to figure out the Star Wars theme or find a hidden musical message in Counter Strike control buttons.
http://thebatman.net/keybored/
59. Make Your Office Ergonomic
Face it–you spend a lot of time at your desk. You might even have a few extra pounds and pallid skin to show for it. While those things are temporary, far to common and more serious is the carpal tunnel, eye strain, and back problems you’ll develop from having a poor workspace.
Hit up this link to create a body-friendly workspace that will keep you limber and flexible: http://www.ergotron.com/tabid/305/language/en-US/default.aspx
60. Adding a Third Monitor
Studies show that dual monitor increase work productivity by 30%. As a geek, you’ll need a third monitor to equal the dual setup of a layman (if that makes sense). While any hack with a VGA port can add a second monitor, it takes a true geek to add a third (or more). This will vary based on graphics/OS, so hit up Google for a tutorial or two.
61. How to Convert a DVD to x264 (or XviD or DivX)
It might seem like child’s play to you, but many individuals do not understand the fine art of converting a DVD into a digital file, let alone the careful skills it takes to achieve a happy balance between size and quality.
Here is an excellent tutorial demonstrating how to rip a DVD with the multi-platform free software Handbrake: http://howto.diveintomark.org/ipod-dvd-ripping-guide/
62. Flash System BIOS
Ya gotta do it some time, so stop putting it off and man up. Flashing the BIOS on your laptop might seem scary (as it should–fear keeps you on your toes and prevents mistakes), but it’s not (actually, it is, but if you even understand why you need to do this, you’ve gotta have at least a few chops by now). Warning–you can seriously bork your computer doing this!
http://www.pcstats.com/articleview.cfm?articleID=1605
63. How to Irrecoverably Protect Data
TrueCrypt, my friends. Learn to use TrueCrypt. If you have ask why, you don’t need it.
64. The Fastest way to Kill a Computer
It’s said that you have to get into a killers mind to understand their weaknesses, right? Same goes for the unfortunate boobs who always kill their laptops. Here’s a list of all the different ways you can accidentally kill a computer–arm your family and friends, and save yourself grief (because it’s surely you they will call when something goes horribly, horribly wrong).



Love this blog I’ll be back when I have more time.
Great list man. In fact this is what every tech geek must know. Though these are simple things, many dont know it.
ITS pretty nice and useful information.
u told us how to lock the computer bt didn’t explained how to unlock it. Does it works for Rackmount monitors using USB Extender
To unlock the machine you just need to put the USB stick back in and restart the machine. Ofcourse your BIOS should be set to boot from USB.
https://caintechnews.wordpress.com/page/3/
There are only three responses to this? really? that’s seriously uncool. I, for one, think this is great stuff.
I must agree this aritical is superb. I like the rest of the site too. I tryed the slipstreaming I read on this site and it worked really well.
http://www.colonelradioshow.co.uk
It’s Peer to Peer, brainiac.
Good stuff.. did you actually solder your glasses?
Yes. 8)
Just one word – WOW!
2 words: Thank. U.
this blog is pure genius, i have always wanted 2 learn how 2 hotwire a car. i willl b recommending this 2 fellow geeks here in hawaii!
That was a terrific article. It was everything you wanted to know about “Geekdom” but was afraid to ask. Frankly, I wouldn’t know who to ask. Nice work! Thanks.
applian, screw that. Use windows version of safari, open activity and find the biggest file and double click it then click save and you’ll save the streaming video to your hdd for free. Or if you use firefox use video downloadhelper
15. Rip Streaming Videos
How to do it without downloading software?
1.Get Firefox
2.View video clip you want to download
3. Type “about:cache?device=disk” (without speech marks) in URL field, or browse to your cache on your system files
(/home/USER/.mozilla/firefox/PROFILE/Cache on linux, I assume C:/Program Files/Mozilla Firefox/PROFILE/Cache on windows)
4. Look for the video clip on the about:cache page (or system folder).
Use Search to find a specific detail (e.g. website URL or “.flv” “.swf”). (Or, using Chris’ idea, search for the biggest filesize)
5. On the about:cache, click on the link once you found it, then right click and save the new link given. On the system file, copy it to another directory, as the cache is only temporary.
Its it a little bit more a challenge to find the video you’re looking for in the cache (especially if you have a large cache), so you might want to clear your cache, then reload the video page, and view the cache. Then, only the items on that new page will be in there, including the video you want to download.
No need to install any programs (apart from firefox), no need to pay for any expensive products.
All though this is a good idea “B” not everyone has Firefox or even wants it. Also this would work in older versions of Firefox but in version 3.5.6 you are unable to right click and save the new link.
The whole point of the post is things you should know, not for yourself exactly but to convey to others that are less knowledgeable than yourself.
Thanks for the comment
Kool tips!
I’ve been on this page for 3 days now… thanks 😛
Brilliant! Having all of those security points will also save potential risk for ID theft too. Those key loggers are prevalent on library rigs, but honestly….if you are reading this…you aren’t at the library, unless you are sniping their wi-fi.
Excellent!
I have used key loggers myself. A friend of mine asked me to check what her son was writing to his friends on MSN as he was getting into a lot of trouble and she thought it could be some of his friends online that was encouraging him. However he knew how to clear the MSN records as he was a bit of a techie kid. He also know what was running on his machine, so putting a screen capture program on there would have just gave it away.
I slipped a little key logger on the back of his machine and being a 13 year old boy he didn’t go under the desk to clean up much. The key logger had 20Mb of storage on it and it sat there for a month and we got the info we needed.
P.s. It was his so called friends on MSN that was influencing him into thing.
@”B” Sah-WEET! (slaps back to serious reality) I offer my gratefulness. (bows and leaves room)
So many of these things rely on or require a small third-party program. Big whoop.
I want to add the following… every geek should know “IT Crowd”
i know it. can’t say i like it. it tries too hard.
Normally I don’t respond, but for this one I make an exception: Thanks! Just wanted to say that.
One point of critique, but it’s probably me to blame: How come I found this site (and blog) not earlier? 😉
Not gonna lie! I wasn’t exactly a geek or nerd in Highschool (a little self denial lol) but this is a solid post for any all those popular kids who now have geeky obsessions… I’ll definitely be going through this list and adding a couple of these cool hacks to my “to-do” list…
Glad to see its tech geek and not sci-fi geek
I manage a web filter at work. Websense does not make it. If you dont want to be filtered on my network, you’d better use an aircard. I was considering writing a bit about it, but if you look up the capabilities of BlueCoat and IronPort, you’ll get an idea of what an enterprise web security proxy will buy you.
Also, websites using CDNs cant be accessed via IP address because many many websites are served up locally from a single subnet’s worth of addresses.
Why is this old meme on digg?
Thanks man!
Awesome, love it!
There’s a major issue with the use of the word “security” in the article under #4.
Tor is for *anonymity*, but since the exit nodes are capable of seeing any unencryped traffic, and as most tor exit nodes are run by “somebodies” (criminals, spooks/intelligence agencies and law enforcement have been spotted), referring to tor as a secure means of communications is very incorrect.
That is, Tor is for hiding the origin of traffic, not its content.
Really amazing things. I bookmarked some of them. Thanks.
65. Use DBAN (Darik’s Boot and Nuke) to securely erase hard disk contents before selling or recycling.
brilliant, i return this page 4th time, and every time i learn something new and different.
Brilliant!
What a great collection. I made this one of my three links today at my Other Thought for the Day blog:
http://otherthoughtfortheday.blogspot.com/2010/02/02-04-required-geek-news-reporting-semi.html
All the best, Ted
Photoshop skills and video editing is valuable to any geek.
Hello. nicejob. I did not expect this site on a Tuesday.
Some website blocks detects IP address too.
Please help!! ive been trying to find the IP adresses for the websites and ive gotten the first step, but when i type it in it just says Request Times Out and smthn about Packets sent, please help me!!
KOO, You can find an IP address by just pinging the site, here’s how:
Start>Run type ‘cmd’ in the black window that now appears type:
ping http://www.nameofsite.com or whatever the site URL is and press enter.
If the site exists you will see the reply ‘pinging http://www.nameofsite.com [212.58.251.195]with 32 bytes of data:
and then some stats, the numbers in the brackets is the IP address.
I felt in love with your article 🙂
Thank you so much !
Enjoyable read. Made my night before bed. (it’s 12:55am on February 13). Some tips were repeats, tho’ they do remind me to always stay on top of my game, so to speak.
Keep up the good work.
great list bookmarked it
Great work! I bookmarked it.
I can relate to this really easy, thank you. I have subscribed to your RSS.
Or you could just learn how to google?
You say stripping DRM is illegal. But that depends on where you are, not everyone lives in the US. In some countries you have a legal right to play your music on any player you own. Stripping the DRM out if that is a necessity to make it playable on another player is then not illegal. Of course I am not a lawyer and this is not legal advice.
SO, Kevin… if you admit not being a lawyer why do you bother giving advice about legal matters? WHile it is true that in a few places stripping the DRM is not illegal, in the majority of places it IS….
Accept the great stuff found here for what it is and follow the advice of R.A.H.: “A critic is a organism which creates and contributes nothing, yet feels it is entitled to judge the work of those who do”.
Great article, I think I was able to fit and do most of the things. I saw your link and article for logging on to a password protected computer. I did a step by step article on how you can log on to any Windows computer, without knowing the password and without RESETTING the password, so basically how you can log on to any Windows Computer without knowing the password and without changing anything on the computer. If you are interested, you can read up on it at: http://indiawebsearch.com/content/logon-to-any-password-protected-windows-machine-without-knowing-the-password
And just for the edification of Geeks and Nerds everywhere… if you EVER need to utilize your geekiness in order ot make a living, I can personally recommend the Geeks and Nerds (GaN) Corporation, in Huntsville Alabama. This is NOT a joke. GaN handles all sorts of ‘geekish’ endeavors, primarily (but not solely) for the US Govt. Check it out. “www.gancorp.com”.
Ah, and if the “Alabama” part scares you, Huntsville is the home of both NASA and US Army missile technology development. Again, no joke. One of two remaining Saturn V missiles is at the US Space and Rocket Museum, in Huntsville… the ‘Space Center’ is also home to Space Camp, of movie “fame”.
What can it hurt to look?
awesome article, love it
I just realised, there are sixty four things. Wow.
Bout #3…. how can I make my own lil icon for this shortcut? :3
I see that I know some skills in your post, that is mean I’m a Geek 😉
I like your post very much.
Keep blogging.
I have a question, if I ping two different URLS and they seem to have the same IP address, what does that mean?
This would be what is called web forwarding, here is an example:
Open command prompt and type:
ping http://www.caintech.co.uk this will resolve to 213.171.195.53
Now type
ping http://www.slipstreaming.co.uk this will also resolve to 213.171.195.53
This is because both URL’s are forwarded to https://caintechnews.wordpress.com which is the real URL of my site.
So that is how you get two URL’s with one IP address. Make sense?
http://thevideogametester.com is game testing site
The link to KeyBored doesn’t appear to be working. I tried clicking it and typing in the site name but it gives me a site that says “This page is parked free, courtesy of $1.99 Domain Registrations, Renewals and Transfers from DomainGoRound”
Doh!
i like this article,.Will check them out.Thanks
nice!
Brilliantly geeky. Hilariously geeky. Much appreciated!
just to notify all that see this, unless your school uses it’s own block, most common blocks have incorporated an IP block
it is awesome……………………
Runes Of Magic – Лучший обзоры онлайн игр.
You’re making a lot of great points during this blog post however it is very hard in my opinion to concentrate on this article on the complicated page design.
I am very thankful to this topic because it really gives useful information ,:~
amazing post,.
Hmm, very informative. I never knew that there’s a way to control a house lights with a personal computer.. That’s cool 😛
After I complete the list, Am I already a Full-Fledge Geek Yet? =D
i knew or had done everything bar hot-wiring a car and soldering glasses i believe. quite impressed myself. although i am a net-sec student and alot of this was networking.
WAUW! I’ve never even thought about trying this kind of stuff, but I’m sure to be checking out some tutorials and try some stuff’ myself!!
One thing, you forgot to add a link for ‘keyboard shortcuts’. nr 42 on the list
This really is a wonderful list, not one of those stoopid ones. I like it.
EEEEK Now I know I am not a Geek I will leave it to you pros.
Thanks
Vanda
Super Post thanks for sharing
Yes that was very nice post
I love this list. Already bookmarked!
Tomorrow geekdom – yippeeee
Some of your links aren’t working any longer. Otherwise great stuff. gotta love Stumble, always brings me to what I didn’t know I wanted to know 🙂
Thanks for the heads up I will try and sort out those dead links.
Damn you, I can’t leave and I need to go to work. Oh well, guess I can look for a new job next week.
Pretty good work for an old bald headed guy.
WOW This must have taken you ages to write. I take my hat off to you. Thanks for all these tips, there were about 20 that I had been meaning to learn but never bothered taking the time to figure it out. Have bookmarked and will be visiting again ^^ too much information for me to get though in only one sitting.
Ya truly the words of a geek but this is what we are, Cool !!
I am New to the computer! And always asking questions to my Kids. They know a lot about It. “BUT” they Show Me, but they CAN’T really TELL Me “HOW IT WORKS”. I NEED to Know what IT is doing on the Inside, Before I Know and Remember what I am doing. Thank you ! this could get Me off to a good start!
I have a question regarding obtaining the IP address for websites. How do you find them using a linux operating system? I’ve been trying to discover how using terminal, but I haven’t been very successful. Any help would be great.
Hi Brant,
Here is a post just for you http://wp.me/pu4Ll-Cv
This is fantastic! And a resource for a budding padawan at things geeky, as you so aptly put it! Love your sense of humour here as well. I’ll be coming back to visit this blog often, methinks! 🙂
The link to Cracking Wifi doesn’t work. Just a heads up. Awesome information, thank you.
Thanks Everett,
I’ll see what I can do.
oh what a great tool stumbleupon is for taking me straight to this blog, love, it will use a lot. good job
this article is so cool. Nerd Approved!
When I save command.com as cmd.bat – and then try and open it – the window flashes offscreen instantly. What.s up with that?
you need to create a bat file with this code:
@echo off
:again
start cmd
This will open a command prompt and keep it open.
http://www.youshouldhavealsoseenthis.com/
Nice list
You missed hacking into a highway sign. My dream is to make one say “All your base are belong to us.”
cool thanks for Reisadvies sharing! btw are there feeds in your blog? I want to add these to my reader Finnaly i came across your postkeep blogging Damn ! I just found a mistake in your website! See if css is managed right!
I’ve tried making cmd.bat on my windows 7 computer, but when the program is opened, the system seems to shut it back down immediately. How do I a) keep the program open/view the open program if my system keeps shooting it down? or b) access the terminal directly, with little/no interference from windows 7? I have some (a little) experience using a terminal directly on Apple products, but I’m not sure how well the second option would go. Any advice?
you need to create a bat file with this code:
@echo off
:again
start cmd
This will open a command prompt and keep it open.
How do I unlock an ipod touch without knowing the password or hooking it to a computer or losing all the information??
Hi Jason,
Unfortunately the only way to complete this is to plug your iPod into a PC, follow the instructions bellow:
Connect your iPod to the primary computer you use it with (the first one iPod synced with), and open iTunes. When you disconnect iPod from the computer, it will no longer be locked.
If you can’t unlock iPod using either [the code or connecting it to the computer you use to manage its songs]. . . you can restore your iPod to factory settings using iPod Updater. Please note that this will erase all data on your iPod. Afterwards, you can add your music and data back to your iPod.
If you want to change the primary computer that your iPod is associated with, do this:
1. Restore your iPod. Warning: The restore process cannot be undone. All of your songs and files will be deleted. Always make a backup of your important data.
2. Connect your iPod to the computer that you want to be the primary computer.
3. Open iTunes and synchronize.
Apple also notes that company “representatives cannot unlock an iPod if you forget your combination. If you can’t unlock your iPod and you don’t have access to the primary computer, your only option is to restore the iPod, which will erase all music and data.”
Thank you a bunch for sharing this with all people you really recognize what you are speaking about! Bookmarked. Kindly additionally visit my web site =). We could have a link trade contract among us
number 11 has a dead link, but you can find the article here at : http://www.ehow.com/list_7225818_5-off-crashed-hard-drive.html
Thanks for the list!
Thanks JD Gold, I have updated the link
Great share man!!!
This is really useful for me and great useful tips…
I write very good. I am free. I better get it written. Thank you!!
Reblogged this on infoinno.
Many thanks, nice site BTW
Thanks! Still trying to get used to the whole blogging thing.
lol, me too
Great list, I like how you included hotwiring a car; definitely more for the hardened geek, lol…I’m also up to 4 monitors so definitely representing.
I like this post. It has many useful informations
Reblogged this on shadowvigil.
Now we all know bypassing passwords is the more fun way to mess with friends.
one thing to say: AWESOME
Hello, i read your blog from time to time and i own a similar one and i
was just wondering if you get a lot of spam feedback? If so how do you protect against it, any plugin or anything you
can recommend? I get so much lately it’s driving me mad so any help is very much appreciated.
HI, I do get some but the built in filter for WordPress normally takes care of it.
As your site is a shopping site you will always be the target for the junk mail unfortunately
Try these plugins to help
http://wordpress.org/extend/plugins/stop-spammer-registrations-plugin/
http://wordpress.org/extend/plugins/akismet
fantastic. reposted on Home
hey the wifi password link is not working.. can u provide any substitutes for that??
Thanks for the heads up Kunal, I have uploaded the original PDF to resolve this.
Also that a goo VPN towers over a PROXY in security…
This is really a good article
pls checkout my blog
http://technopcamd.blogspot.in/
I love the cracking & hack pop. Tats seriously interesting. Loved this blog with innovative stuff.
For American geeks- #1 The Metric System.
“SATA – Serial ATA” If we all need to know this to be true geeks, what does the “ATA” stand for?
Hi Joe,
Thanks for reading my blog, the answer to your question is as follows:
ATA short for Advanced Technology Attachment, a disk drive implementation that integrates the controller on the disk drive itself.
There are several versions of ATA, all developed by the Small Form Factor (SFF) Committee:
ATA: Known also as IDE, supports one or two hard drives, a 16-bit interface and PIO modes 0, 1 and 2.
ATA-2: Supports faster PIO modes (3 and 4) and multiword DMA modes (1 and 2). Also supports logical block addressing (LBA) and block transfers. ATA-2 is marketed as Fast ATA and Enhanced IDE (EIDE).
ATA-3:Minor revision to ATA-2.
Ultra-ATA: Also called Ultra-DMA, ATA-33, and DMA-33,supports multiword DMA mode 3 running at 33 MBps.
ATA/66:A version of ATA proposed by Quantum Corporation, and supported by Intel, that doubles ATA’s throughput to 66 MBps.
ATA/100: An updated version of ATA/66 that increases data transfer rates to 100 MBps.
ATA also is called Parallel ATA. Contrast with Serial ATA.
I hope this helped
Include – How to remote start a pc via net.
Nice stuff!
forgot one for the old-timers: install a CB radio in a vehicle
haha..cool…not all of them i know
Basics but yet important stuff for a geek.
Reblogged this on BobLovesTech and commented:
Always good for newbies to know
This is the way to fix a phone http://www.plumbworld.co.uk/how-to-fix-a-phone-dropped-in-the-toilet
nice info ever all
Reblogged this on The Black Snack.
Reblogged this on Abhinav's Blog of Reblogs.
That’s a daunting list. Guess I’m not cut out to be a geek. Will try some of the stuff though.